February 16, 2022
In the digital world,
most cyber security threats are self-inflicted
Are the vast majority of cyber-attacks on your company avoidable?
APIs have emerged as the internal connective tissue within an organization and the external connective tissue with customers, supply chain partners, and other key stakeholders.
According to an Akamai study, API communications now account for more than 83% of all internet traffic.
A report released last February by Salt Security showed that 91% of companies had security problems with their APIs. Over a quarter of the companies in the report run critical API-based applications with no security strategy at all.
A comprehensive API strategy is a key foundation for digital transformation. By creating seamless and secure access to APIs, companies can:
- Optimize customer experiences
- Create dynamic digital ecosystems
- Achieve operational excellence
- Build platform business models
Unfortunately, as the examples below amplify, the vast majority of companies do not have a strong, well thought out API strategy to mitigate cyber-security attacks. In fact, their lack of understanding and inaction is the primary source of their vulnerability.
A large healthcare organization in the southeast wanted to build a catalog of all their APIs. Their initial estimate was that the company had 450 APIs, but when they finished their internal audit the number of APIs exceeded 4000.
Joseph Blount, CEO of Colonial Pipeline, told a Senate committee that criminal hackers infiltrated the company’s computers through an old virtual private network (VPN) that was not intended to be in use. The VPN technology was used to allow staff to access the company’s internal corporate network from home and did not require multifactor authentication.
In early May of last year, Peloton announced that it had exposed customer account data on the Internet. Anyone could access users’ account data from Peloton’s servers, even if the users set their account profiles as private. The cause: a faulty API that permitted unauthenticated requests.
Another study showed that more than 80% of developers knowingly release applications with insecure code.
Building an API Lifecycle Management program
In order for companies to have greater awareness and more control of their cyber-security risks, they need to develop a comprehensive API Lifecycle Management strategy and implementation program that:
- Defines the desired outcomes
- API design, selection, management, cost control, & governance programs
- API revenue contribution
- Audits and catalogs all approved APIs
- Provides a governance process for internal and external development, access and usage of APIs
- Internally developed APIs
- Externally outsourced development of APIs
- Establishes a consumption based pricing model
- Develops a set of API performance metrics that:
- Track API usage and systematically retires unused legacy APIs
- Measures and monitors regulated APIs latency, documentation, & compliance of API schema
- Identifies insider threat risks
- Monitors data security including:
- Average time to notification of a breach
- Average time to containment
Organizations need to utilize a broad range of tools, automation, scanning technologies, and telemetry monitoring because there are not enough people to monitor API security manually.
‘Shift Left’ to address security sooner in the development cycle
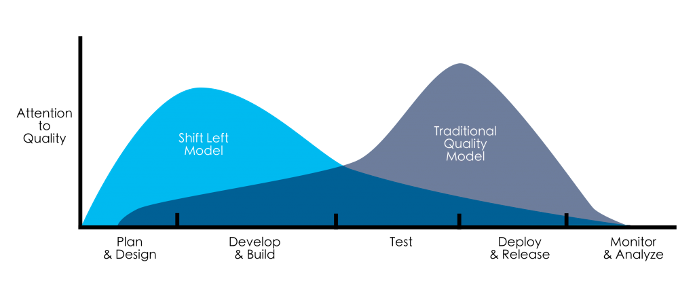
A critical part in reducing your risk exposure is to address security sooner in the development lifecycle which creates a “shift left” development model as shown on the chart above. This shift means building security into the development process during requirements analysis or planning as opposed to when development and testing have already begun.
This shift is an integral part of the emergence of a DevSecOps mentality where development and operations have come together, and security is part of the process from start to finish.
As Justin Dolly, Chief Security Officer at software testing firm Sauce Labs, acknowledges… “bugs in software are inevitable and often unintentional. The sooner that development teams can identify low-quality code, the more likely they are to address the issue during production and avoid releasing a vulnerability.”
Commit to an API-First Security Program

In 2020, the FBI Internet Crime Complaint Center, received a 200% increase in phishing incidents. In order for companies to combat this kind of increased risk vulnerability, they have to adopt an API-First security mindset and action plan.
Some early API-First security adopters are hiring API architects, creating API centers of excellence, and creating governance groups to oversee API policy.
Through my reading and research, here are some additional elements that should be incorporated into an API-First security program:
- Audit and control access & utilization of all APIs
- Web application firewalls
- OWASP vulnerability scanning tools
- Maintain logging of failed request trends to identify attacks
- Encrypt data both at rest and in transit data
- Use Transport Layer Security (TLS) and authentication tokens to transmit data securely
- Prevent credential stuffing
- 1 in 5 attempts to gain unauthorized access to user accounts is done through APIs rather than user facing logins
- Make automated checks standard practice
- Automate security checks as part of a CI/CD pipeline
- Allow the organization to scale security with its product offerings
- Incorporate scanning tools into DevSecOps process to limit unintended exposure of data
- Enact data input validation and rate limiting to prevent XSS (Cross Site Scripting) and DOS (Denial of Service) attacks respectively.
As many of you reading this blog know, there is no silver bullet to successfully prevent cyber-security threats. There is, however, a great deal that can be done to reduce your vulnerability by eliminating self-inflicted wounds.
As always, I am interested in your comments, feedback and perspectives on the ideas put forth in this blog. Please e-mail them to me on linkedin. And, if this content could be useful to someone you know please share it here: